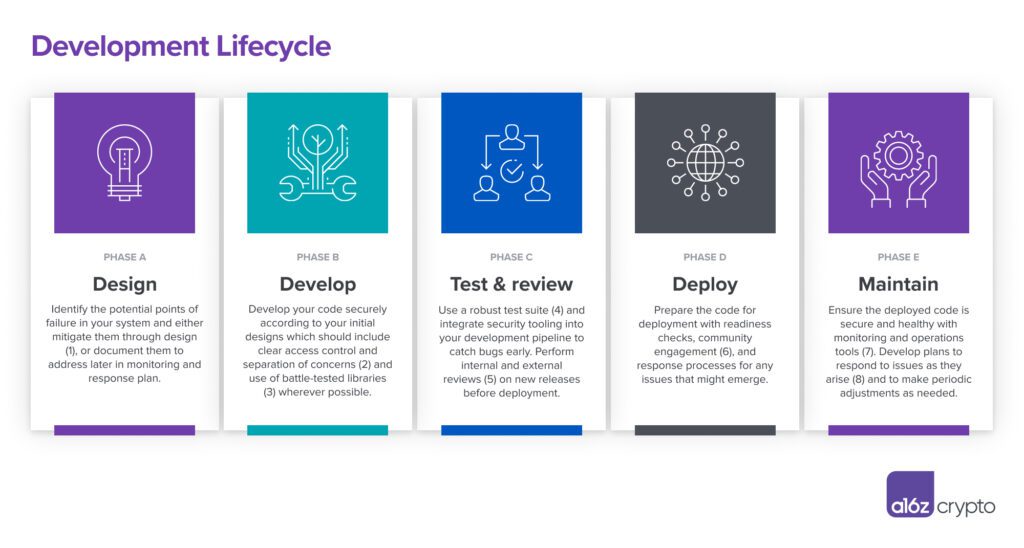
#6: Consider incentivizing whitehat community engagement
- What: Create programs that encourage community participation in security improvement on open-source codebases. One way to do this is by creating bug bounties. Another way is to encourage the community to develop protocol-monitoring detection bots.
- Why: Development teams can benefit greatly from tapping into a wider pool of knowledge and experience. (Again, also the point of where open source helps in crypto.) Notably, such programs can help generate enthusiasm for a project, essentially turning the community and whitehat hackers into evangelists. They can also help turn would-be attackers into security assets by providing paths for hackers to become defenders.
- How: Use bug bounty platforms (such as Code4rena, HackenProof, Immunefi, or Secureum) to fund bounty systems with severity-based rewards that incentivize skilled hackers to safely disclose vulnerabilities. [Full disclosure, some of the co-authors of this post work for Forta, which has a network which offers a tokenized incentive structure for the decentralized creation of high-quality security-monitoring bots.] Development teams can encourage their protocols’ communities to take advantage of both traditional and web3-native approaches to incentivizing bug bounties, and for the participants to potentially profit by enhancing security in a win/win for all.
#7: Consider real-time monitoring
- What: Implement systems that monitor smart contracts and critical operational components such as oracles and bridges, and report suspicious activity to the development team and community based on known threat models.
- Why: Early detection of issues allows a team to respond to exploits and bugs quickly, potentially stopping or mitigating any damage. This seems obvious but can be overlooked in planning.
- How: Use monitoring platforms or distributed nodes to run bots that monitor smart contract events in real-time. Implement dashboards and alert notifications for development teams and the wider community as needed.
#8: Consider incident and emergency response operations
- What: Make use of tools and processes that enable an immediate response in the event of any security issues.
- Why: Even with the best pre-deployment safeguards, it is still possible for smart contracts and critical components, such as oracles and bridges, to have live issues. Having dedicated personnel, clear processes, and appropriate automations in place ensures that incidents can be investigated quickly – and resolved as swiftly as possible.
- How: Prepare for the worst by planning how to respond to incidents or emergencies and automating response capabilities to the greatest extent possible. This includes assigning responsibilities for investigation and response to capable personnel that can be publicly contacted about security issues via a distributed security mailing list, instructions in the code repository, or by a smart contract registry. Based on the protocol’s threat models, develop a set of processes that could include scenario drills and expected response times for taking emergency actions. Consider integrating automation into incident response: for example, tools can ingest and act upon events from Forta bots.
***Security considerations should be an integral part of successful development – not just an afterthought or add-on. While this framework shares some quick guidance for those building web3 protocols and applications to promote security throughout the development process, no short overview can provide an exhaustive discussion of all aspects of smart contract security. Teams lacking in-house security expertise should reach out to qualified web3 security experts who can assist them in applying the general guidance above to their specific situations. But above all, remember that security is never just a simple matter of ticking boxes in a simple checklist manifesto to manage complexity; as such, it’s always going to be a never-ending, ongoing set of best practices. We’re still at the beginning of establishing these best practices, so now is the time to collaboratively create and share them, at all levels for all developers.
Editor: Robert Hackett @rhhackett
***
Andy Beal is the ecosystem lead at Forta. Previously, he helped manage EY’s blockchain practice.
Nassim Eddequiouaq is the chief information security officer for a16z crypto. He previously worked at Facebook, Anchorage, and Docker.
Riyaz Faizullabhoy is the chief technology officer for a16z crypto. He previously worked at Facebook, Anchorage, and Docker.
Christian Seifert is a researcher-in-residence at Forta. Previously, he spent 14 years working on web security at Microsoft.
***
The views expressed here are those of the individual AH Capital Management, L.L.C. (“a16z”) personnel quoted and are not the views of a16z or its affiliates. Certain information contained in here has been obtained from third-party sources, including from portfolio companies of funds managed by a16z. While taken from sources believed to be reliable, a16z has not independently verified such information and makes no representations about the enduring accuracy of the information or its appropriateness for a given situation. In addition, this content may include third-party advertisements; a16z has not reviewed such advertisements and does not endorse any advertising content contained therein.
This content is provided for informational purposes only, and should not be relied upon as legal, business, investment, or tax advice. You should consult your own advisers as to those matters. References to any securities or digital assets are for illustrative purposes only, and do not constitute an investment recommendation or offer to provide investment advisory services. Furthermore, this content is not directed at nor intended for use by any investors or prospective investors, and may not under any circumstances be relied upon when making a decision to invest in any fund managed by a16z. (An offering to invest in an a16z fund will be made only by the private placement memorandum, subscription agreement, and other relevant documentation of any such fund and should be read in their entirety.) Any investments or portfolio companies mentioned, referred to, or described are not representative of all investments in vehicles managed by a16z, and there can be no assurance that the investments will be profitable or that other investments made in the future will have similar characteristics or results. A list of investments made by funds managed by Andreessen Horowitz (excluding investments for which the issuer has not provided permission for a16z to disclose publicly as well as unannounced investments in publicly traded digital assets) is available at https://a16z.com/investments/.
Charts and graphs provided within are for informational purposes solely and should not be relied upon when making any investment decision. Past performance is not indicative of future results. The content speaks only as of the date indicated. Any projections, estimates, forecasts, targets, prospects, and/or opinions expressed in these materials are subject to change without notice and may differ or be contrary to opinions expressed by others. Please see https://a16z.com/disclosures for additional important information.