Apple iCloud: Doing this 1 thing can help stop hacks
Attackers are on a tear targeting people’s iCloud accounts, especially those of crypto owners. While most of the literature on the subject warns of shoulder surfers – snoops glancing over people’s shoulders to steal iPhone passcodes – we’re noticing a different and more troubling trend: remote takeovers of iCloud accounts.
In this post, we’ll draw from our firsthand experience helping people protect against – and react to and recover from – iCloud hacks. We’ll put you in the shoes of someone who’s digital world is unraveling. The goal is to show you what typically happens during a remote iCloud account takeover, and then we will tell you how to help prevent something like this from happening to you. (Hint: Set a recovery key.)
What it’s like to have your iCloud account hacked remotely
It all starts with a strange notification on your phone.
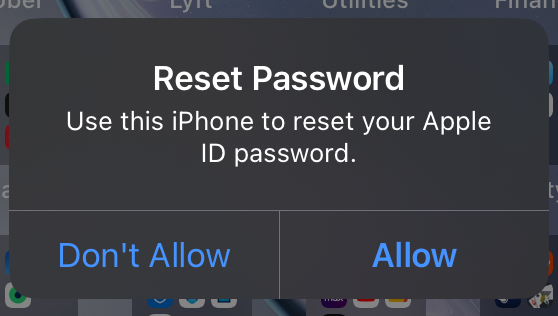
Hm, that’s odd, you think. You didn’t initiate an iCloud reset, so you click Don’t Allow and go on with your day.
Except a few moments later you get a text.
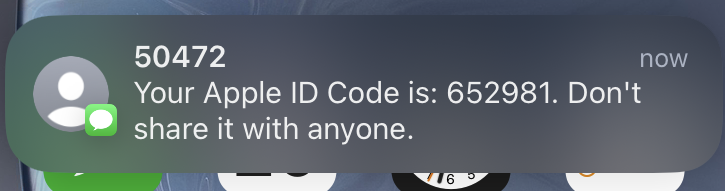
Strange – seems related. Still, you don’t know what to do, so you ignore it and hope it goes away. After all, what else can you do? While pondering this, you get an email.
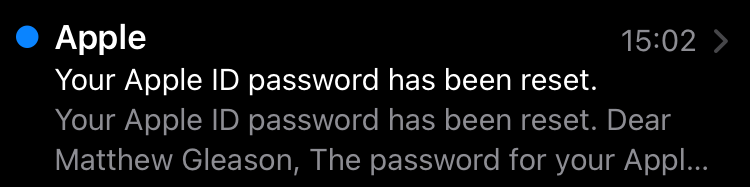
OK, you realize, this is bad. What’s happening? Did you click the wrong button when you were asked to reset your password? You don’t think so. But maybe? You don’t know what else to do, so you act on your only and best idea: log into iCloud to change your password.
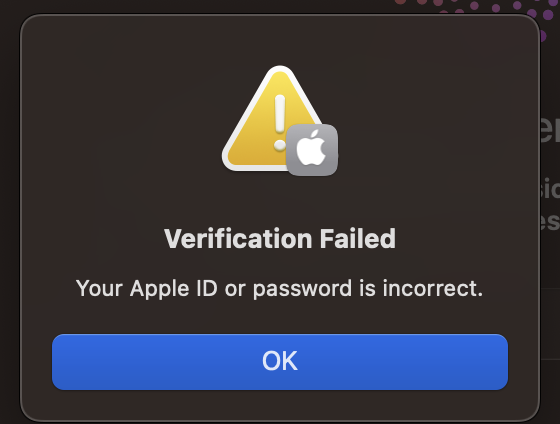
Maybe you just entered your password wrong. You try a few more times, but attempt after attempt fails. Thankfully, Apple has a way around this. You’ll just say you forgot your password.
Going through the password reset flow on your computer, you enter your email and then your phone number…
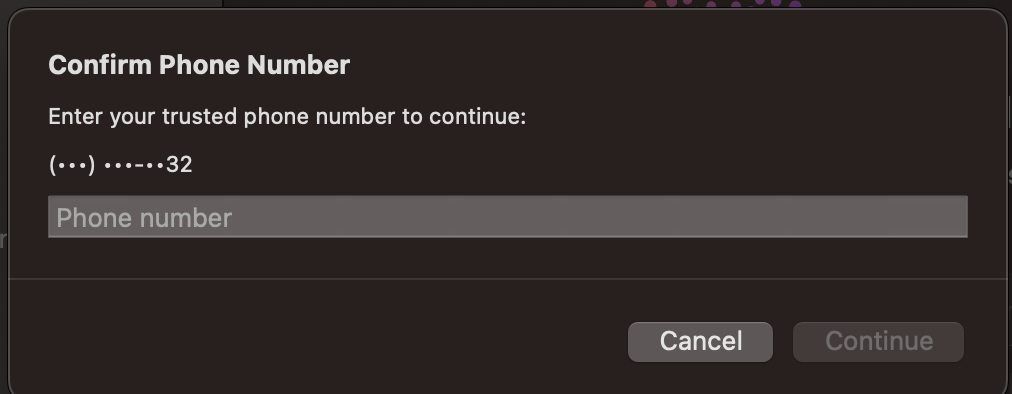
Except that’s not the last two digits of your phone number. You open your email inbox again. That’s when you see it.
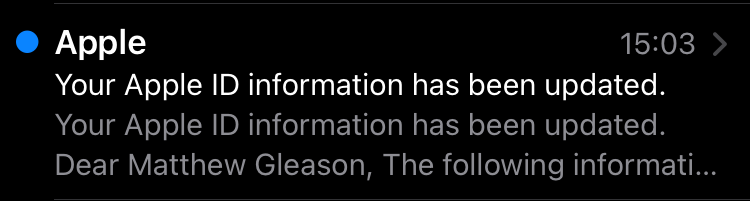
Someone locked you out of your account.
You’ll tell Apple, they’ll solve it.
You visit the Apple support webpage for information on how to regain control of your Apple ID. You read everything. You follow all the directions. You repeat all the steps you already tried.
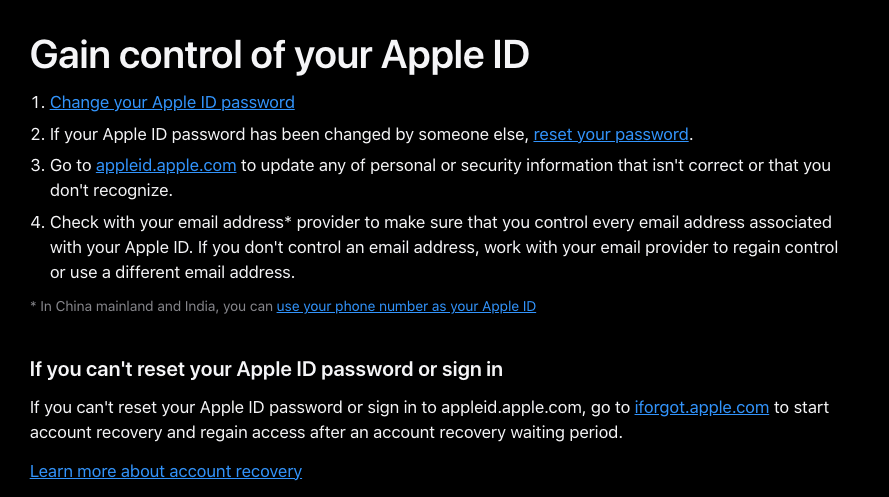
But every time you click the link to “regain access after an account recovery waiting period”, you get the same “confirm phone number” prompt as earlier.
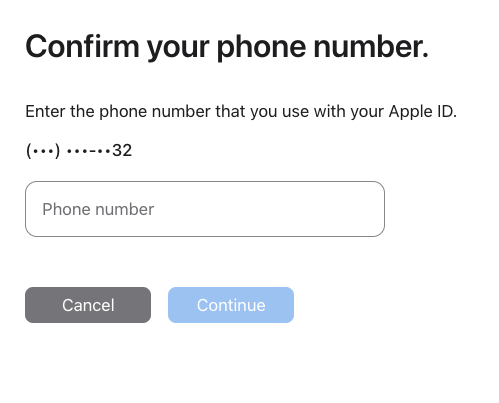
It’s tied to the wrong phone number. You’re at a dead end. There is no way to submit a request beyond this point. No matter how many times you click iforgot.apple.com, you keep getting served the same unhelpful phone number prompt. Frustration mounts. You’re stuck. You’re trying to do what Apple says and you’re getting nowhere.
Meanwhile, some stranger has access to all your data and there’s nothing you can do. Your phone chimes.
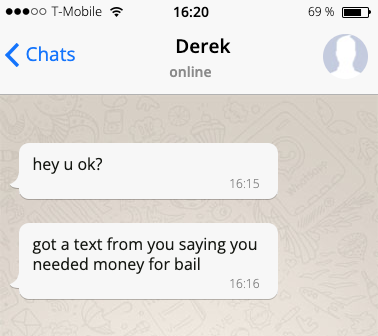
Confused, you reply confirming you’re OK. Your friend tells you that you sent him a plea for bail money. You assure him you’re not in jail and that everything’s fine, except that you’re pretty sure you got hacked.
You call everyone you can think of to let them know that any texts they receive aren’t from you. You don’t want the hacker stealing money from any friends or family. More emails arrive.
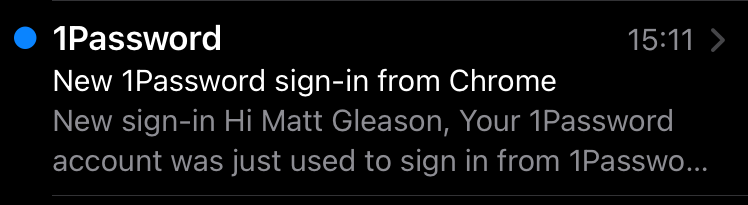
Whoever hacked you is breaking into your accounts one by one. You spend the next hour resetting every password you have. You manage to recover some stolen accounts using password resets that are tied, thankfully, to your email account which remains under your control.
Still anxious, you scour the internet for what else to do. Apple documentation says you can submit a request to get your account back – but the link just keeps asking you to confirm a phone number you don’t know and that’s not yours. Reddit posts tell you how hopeless your situation is (and how it is all your fault). Sketchy Twitter or X or whatever accounts claim they can help if you call them. That’s when it hits you. The sinking realization.
Your account is gone – and you’re never getting it back.
You sleep poorly that night. The next day one of your crypto wallets gets drained. You’re spiraling.
Worse, you realize someone has access to every picture and video you’ve ever saved. This includes photos of your driver’s license, passport, credit cards, and plenty of other things you never intended anyone else to see.
Your stomach drops. Nauseated, you report your cards stolen. You lock your identity from being issued new lines of credit. And you hope – pray – that nothing else happens.
Eventually, life quiets down. It takes time before you’re finally able to put this behind you, to come to grips with your new reality, to breathe more freely. Months maybe.
In time, you recoup money for the fraudulent purchases from the banks and credit card issuers, but the crypto funds are gone for good. You recover some photos – ones you had saved to your device or that were backed up to other cloud services – but you don’t recover all of them. Guess that’s the price you pay for… being you? Anyway, you’re glad to be over wit–
*Ding*.
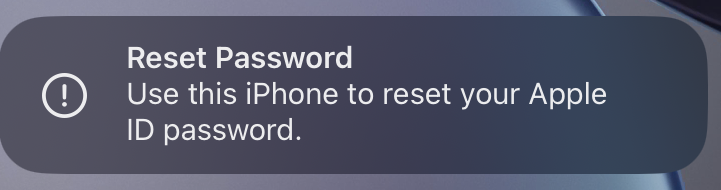
How and why remote iCloud hacks happen
The ending here – a notification signaling another iCloud hacking attempt – isn’t meant just to be cheeky. It’s surprisingly common for someone who has been hacked once to get hacked again, likely by different groups using the same leaked information about the same person.
The scenario narrated above is an all too common experience. It’s a nightmare for anyone, and it is especially so for high-profile crypto people. Why are you getting hacked? Because iCloud accounts contain loads of sensitive information that attackers are after. Here’s just a sample:
- Photos of government documents
- Photos of credit cards
- Crypto wallet seed phrases (usually in Photos or Notes)
- Passwords (in Keychain)
- Apple Pay credentials
- Photos and videos you don’t want released
- iCloud backups
All of these things can be valuable in their own right and make you a prime target. Doubly so if you’re known to be well off or internet famous. Even more so if you’re into crypto.
Here’s what’s going on behind the scenes. Attackers tend to follow the “path of least resistance”, meaning they will do whatever is easiest for them to steal accounts. In this case, attackers are stealing iCloud accounts by using Apple’s account recovery process.
The account recovery process requires access to one of four things:
- Access to an unlocked device logged into your iCloud account
- Access to your text messages
- Access to your phone calls
- Access to someone you’ve enrolled as a trusted contact
The first and fourth methods are opportunistic. Criminals may watch you (or a trusted contact) type a passcode into an iPhone and then steal the physical device in person. That’s obviously a concern – and these incidents do take place – but they’re outside the scope of this piece.
In our scenario, the one we’re seeing most often, attackers are taking advantage of the second and third methods. Specifically, because the security measures of major telecoms tend to be a little lax, attackers will call into your carrier, pretend to be you (or the account holder), and ask for help. (Sometimes they will even bribe telecom employees for access.) If the attackers are successful, they’ll get a new SIM card enrolled for your number or they will have your calls or texts forwarded to their number. This way they can view the recovery codes that get sent to your phone number and they can provide them to Apple when resetting your passwords.
After taking over your iCloud account, attackers don’t immediately gain access to everything. Apple requires the hacker to provide a device passcode before accessing some data such as your Apple Pay information or the passwords stored in your iCloud Keychain. If an attacker has seen you type in your passcode, you’re toast. Otherwise, you better hope an attacker can’t guess your passcode.
Let’s say you’re using your or your dog’s birthday or something else that’s easily guessable, like 102115 (211015 for you Europeans). If so, you’re in trouble. Seriously, use something else! Preferably a random string of numbers. Apple allows people a minimum of 10 passcode-guessing attempts, so choose something unique enough that an attacker won’t be able to guess it before they have to stop. (I’ve heard some cases of Apple support granting as many as 30 attempts.)
Even if the attackers don’t know your passcode, they have access to all your notes, photos, iCloud backups (including iMessage logs), contacts, and more. They’ll use the data contained in every one of these places to try to steal money from you, your friends, your family – and anyone you’re connected to. If the attackers do get lucky and guess your passcode, then they will gain access to every account that has a password stored in iCloud. They’ll use access to those accounts to try to steal more money.
The worst part? Recently, attackers have started to keep the accounts they steal indefinitely. The thieves will change your account’s trusted phone number or set up a so-called account recovery key that only they know to prevent you from ever recovering your account. That means if you use iCloud, you could lose access to thousands of your photos, videos, and more – forever.
How to help prevent remote iCloud hacks
There is something you can do about it: set a recovery key.
The recovery key is a random key generated by Apple that must be provided to reset your account password. If you enable this feature, you’re much less susceptible to the online attacks described above.
Enabling this feature is just the first of two steps though. You need to make sure you don’t lose this recovery key. You might need to use it one day, especially if you lose your devices and iCloud password. Store the key somewhere safe and secure.
Crypto users should already have some familiarity with this level of security. Treat your recovery key as you would a seed phrase, the random series of 12 or 24 words that can be used to recover a crypto wallet. Ideally, that means you should treat it very securely.
Storing a recovery key somewhere even a little secure – like a physical safe or a highly locked down email account – makes your situation a lot better. Based on the attacks we’re observing, this is the single most important thing you can do to protect yourself against the scenario outlined up top.
Enabling a recovery key is easy. Just follow Apple’s instructions here. If you’re using Apple’s Advanced Data Protection, that means you already have this feature enabled and don’t have to worry. Good on you.
Be safe out there.
Read next: PSA: A setup for ‘minimum viable security’
***
Editor: Robert Hackett
***
This content, which contains security-related opinions and/or information should not be relied upon as professional advice, or an endorsement of any practices, products or services. There can be no guarantees or assurances that the views expressed here will be applicable for any particular facts or circumstances, and should not be relied upon in any manner.
The views expressed here are those of the individual AH Capital Management, L.L.C. (“a16z”) personnel quoted and are not the views of a16z or its affiliates. Certain information contained in here has been obtained from third-party sources, including from portfolio companies of funds managed by a16z. While taken from sources believed to be reliable, a16z has not independently verified such information and makes no representations about the enduring accuracy of the information or its appropriateness for a given situation. In addition, this content may include third-party advertisements; a16z has not reviewed such advertisements and does not endorse any advertising content contained therein.
This content is provided for informational purposes only, and should not be relied upon as legal, business, investment, or tax advice. You should consult your own advisers as to those matters. References to any securities or digital assets are for illustrative purposes only, and do not constitute an investment recommendation or offer to provide investment advisory services. Furthermore, this content is not directed at nor intended for use by any investors or prospective investors, and may not under any circumstances be relied upon when making a decision to invest in any fund managed by a16z. (An offering to invest in an a16z fund will be made only by the private placement memorandum, subscription agreement, and other relevant documentation of any such fund and should be read in their entirety.) Any investments or portfolio companies mentioned, referred to, or described are not representative of all investments in vehicles managed by a16z, and there can be no assurance that the investments will be profitable or that other investments made in the future will have similar characteristics or results. A list of investments made by funds managed by Andreessen Horowitz (excluding investments for which the issuer has not provided permission for a16z to disclose publicly as well as unannounced investments in publicly traded digital assets) is available at https://a16z.com/investments/.
Charts and graphs provided within are for informational purposes solely and should not be relied upon when making any investment decision. Past performance is not indicative of future results. The content speaks only as of the date indicated. Any projections, estimates, forecasts, targets, prospects, and/or opinions expressed in these materials are subject to change without notice and may differ or be contrary to opinions expressed by others. Please see https://a16z.com/disclosures for additional important information.