Achieving Crypto Privacy and Regulatory Compliance
Editor’s note: Below is a shorter summary of the paper “Privacy-Protecting Regulatory Solutions Using Zero-Knowledge Proofs” in blog post form. Download the full paper, or read the text here.
The development and regulation of web3 – an evolution of the internet powered by crypto – must achieve two goals that are often in tension. Goal 1: Preserve consumer privacy, despite the default transparent nature of blockchains. Goal 2: Reduce the risk of illicit finance in the interest of national security. We believe these ends are simultaneously achievable.
Web3 cannot achieve its full potential unless blockchains support private transactions. If interacting with a blockchain means exposing sensitive financial information, such as salaries, payments for medical treatments, and payments to suppliers, people will be reluctant to use these systems. Ultimately, the question is how to enable people to use privacy-enhancing web3 technologies (good), while discouraging bad actors from abusing those same technologies (bad).
Early attempts leave the market wanting. The U.S. Department of the Treasury’s Office of Foreign Assets Control’s (OFAC) recent enforcement action against Tornado Cash underscores the predicament. In August, OFAC sanctioned wallet and smart contract addresses associated with Tornado Cash, a popular privacy-preserving service for Ethereum, in response to more than $7 billion worth of virtual currency laundered through the service since 2019. Notably, the laundered transactions included over $455 million stolen by the Lazarus Group, a Democratic People’s Republic of Korea (DPRK) state-sponsored hacking group.
While Tornado Cash had some technical controls in place to guard against illicit financial activity, those controls failed to prevent significant volumes of illicit funds from running through the service. As a result, we consider here whether more comprehensive controls could be more effective.
Zero knowledge proofs, a cryptographic innovation that enables auditable security without undermining secret-keeping, is one solution to reconcile consumer privacy and regulatory compliance. At its core, a zero-knowledge proof is a way for one party, called a “prover,” to convince another party, a “verifier,” that a certain statement is true, while revealing nothing about the underlying data that makes the statement true. Zero knowledge proofs are powerful tools for preventing the abuse of privacy-preserving web3 protocols.
Further, a combination of three approaches using zero knowledge proofs may offer better safeguards. First, deposit screening, or checking wallets that are attempting to deposit funds against blocklists and allowlists. Next, withdrawal screening, or checking wallets that are attempting to withdraw funds against blocklists and allowlists. Finally, selective de-anonymization, a feature that would provide federal regulators or law enforcement access to transaction details. While none of these approaches alone is a silver bullet, taken together they may improve the ability to detect, deter, and disrupt illicit financial activity and prevent the use of privacy protocols by sanctioned state actors, all while preserving privacy for good actors.
Below we offer a high-level overview of the available options. A more comprehensive and in-depth discussion of the regulatory issues at hand and the nuances of each technological approach is available in our full paper, which you can find here.
-
Deposit screening
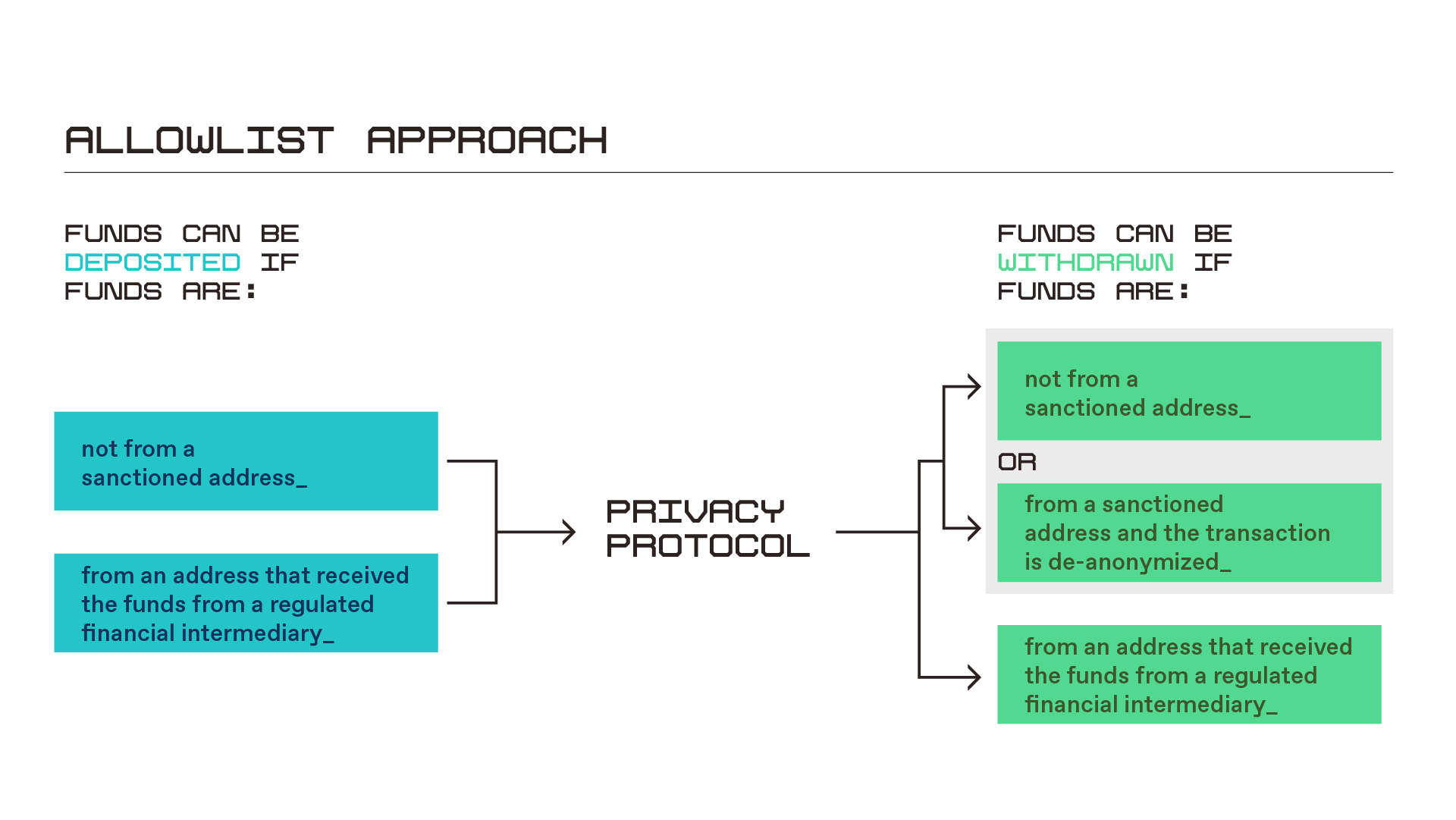
The first approach involves screening wallets to prevent deposits of assets coming from sanctioned entities connected with exploits, hacks, or certain other illicit activity. This could involve government-hosted blocklists as well as on-chain oracle services, or data feeds, provided by blockchain analysis firms. A privacy protocol’s smart contracts would “call” the relevant blocklist contracts before accepting funds into one of its pools, and deposit requests would fail if the funds are from a blocked address. One could also couple this with an “allowlist” approach, making it easier for funds to be deposited from addresses that received funds from regulated financial intermediaries, such as cryptocurrency exchanges, as shown in the graphic below. Deposit screening is a good first step, but is incomplete in isolation, as we discuss more fully in our paper beginning on page 11.
-
Withdrawal screening
Withdrawal screening is similar to deposit screening, except instead of checking the wallets of inbound funds against blocklists, the cross-referencing happens just before withdrawal. Funds originating from flagged wallets would remain frozen, unable to be withdrawn. Fear of losing proceeds acts as a deterrent to would-be launderers. Withdrawal screening can address some of the shortcomings of deposit screening. For example, since privacy-preserving protocols more effectively anonymize their sources the longer they hold funds, blocklists may be updated during the intervening time period, making it more likely that sanctioned property will be identified and frozen. But, there are challenges associated with both types of screening, as our paper details on page 14.
-
Selective de-anonymization
Selective de-anonymization is a third approach that could be incorporated in order to address practical challenges associated with privacy-protecting protocols. The method comes in two flavors: voluntary and involuntary.
Voluntary selective de-anonymization
Voluntary selective de-anonymization allows people to reveal the details of transactions to selected or designated parties. The option can be useful for people who believe they were erroneously added to a sanctions list. The method offers a way for them to reclaim frozen funds. But the approach may reduce the effectiveness of withdrawal screening as a deterrent since bad actors could withdraw funds merely by de-anonymizing their transactions. In these scenarios, however, illicit users would receive no benefit at all from having used the privacy-enhancing service. Our paper treats the option in greater depth starting on page 14.
Involuntary selective de-anonymization
Involuntary selective de-anonymization is the nuclear option. The approach would provide the government with the ability to track and trace illicit proceeds upon presentation of a valid warrant or court order. The challenges associated with this approach are manifold: Who will maintain the private keys that unlock traceability? How will key-keepers ensure keys can’t be stolen or abused? These questions come up in every discussion of key escrow, which is what involuntary selective de-anonymization is. This solution is perennially unpopular and rife with operational challenges – the idea of a “back door.” Nonetheless, in the interest of comprehensiveness, we present the idea here as an option that may be considered. See page 15 in our paper for a richer discussion of the approach.
Conclusion
While not opining on the appropriateness of implementing restrictions at the protocol layer of the web3 tech stack, we do believe that mitigating measures could apply at the app or client level of software frontends. Developers should have a full understanding of the available tools that might limit exploitive use by cybercriminals and state actors who threaten national security, thereby exposing such protocols to potential regulatory action, as experienced by Tornado Cash. Taken together, the measures discussed here – deposit screening, withdrawal screening, and selective de-anonymization – could help mitigate national security concerns and protect consumer privacy in web3.
Download the full paper, or read it here.
***
Editor: Robert Hackett
***
Joseph Burleson is an associate general counsel at a16z crypto, where he advises the firm and its portfolio companies on legal, governance, and decentralization matters.
Michele Korver is the head of regulatory at a16z crypto. She previously served as FinCEN’s Chief Digital Currency Advisor, DOJ’s Digital Currency Counsel, and as an Assistant United States Attorney.
Dan Boneh is a senior research advisor at a16z crypto. He is a professor of computer science at Stanford University, where he heads its Applied Cryptography Group; co-directs the Stanford Center for Blockchain Research; and co-directs the Stanford Computer Security Lab.
***
The views expressed here are those of the individual AH Capital Management, L.L.C. (“a16z”) personnel quoted and are not the views of a16z or its affiliates. Certain information contained in here has been obtained from third-party sources, including from portfolio companies of funds managed by a16z. While taken from sources believed to be reliable, a16z has not independently verified such information and makes no representations about the current or enduring accuracy of the information or its appropriateness for a given situation. In addition, this content may include third-party advertisements; a16z has not reviewed such advertisements and does not endorse any advertising content contained therein.
This content is provided for informational purposes only, and should not be relied upon as legal, business, investment, or tax advice. You should consult your own advisers as to those matters. References to any securities or digital assets are for illustrative purposes only, and do not constitute an investment recommendation or offer to provide investment advisory services. Furthermore, this content is not directed at nor intended for use by any investors or prospective investors, and may not under any circumstances be relied upon when making a decision to invest in any fund managed by a16z. (An offering to invest in an a16z fund will be made only by the private placement memorandum, subscription agreement, and other relevant documentation of any such fund and should be read in their entirety.) Any investments or portfolio companies mentioned, referred to, or described are not representative of all investments in vehicles managed by a16z, and there can be no assurance that the investments will be profitable or that other investments made in the future will have similar characteristics or results. A list of investments made by funds managed by Andreessen Horowitz (excluding investments for which the issuer has not provided permission for a16z to disclose publicly as well as unannounced investments in publicly traded digital assets) is available at https://a16z.com/investments/.
Charts and graphs provided within are for informational purposes solely and should not be relied upon when making any investment decision. Past performance is not indicative of future results. The content speaks only as of the date indicated. Any projections, estimates, forecasts, targets, prospects, and/or opinions expressed in these materials are subject to change without notice and may differ or be contrary to opinions expressed by others. Please see https://a16z.com/disclosures for additional important information.